General problem description
For this challenge we got a picture of a Lego Mindstorm EV3, which displays the flag partly (see below).

And we also got a pcap (OK, it was in the apple PackageLogger format) with captured Bluetooth transmission.
Solution
The pcap shows Bluetooth traffic, and wireshark finds furthermore identifies RFCOMM protocol. Some of them includes additional data parts.
If you dig around long enough on the internet you can find a wireshark dissector written for the Mindstorm EV3 communication protocol.
If we load this dissector we can easily identify the commands sent to the Mindstorm device.
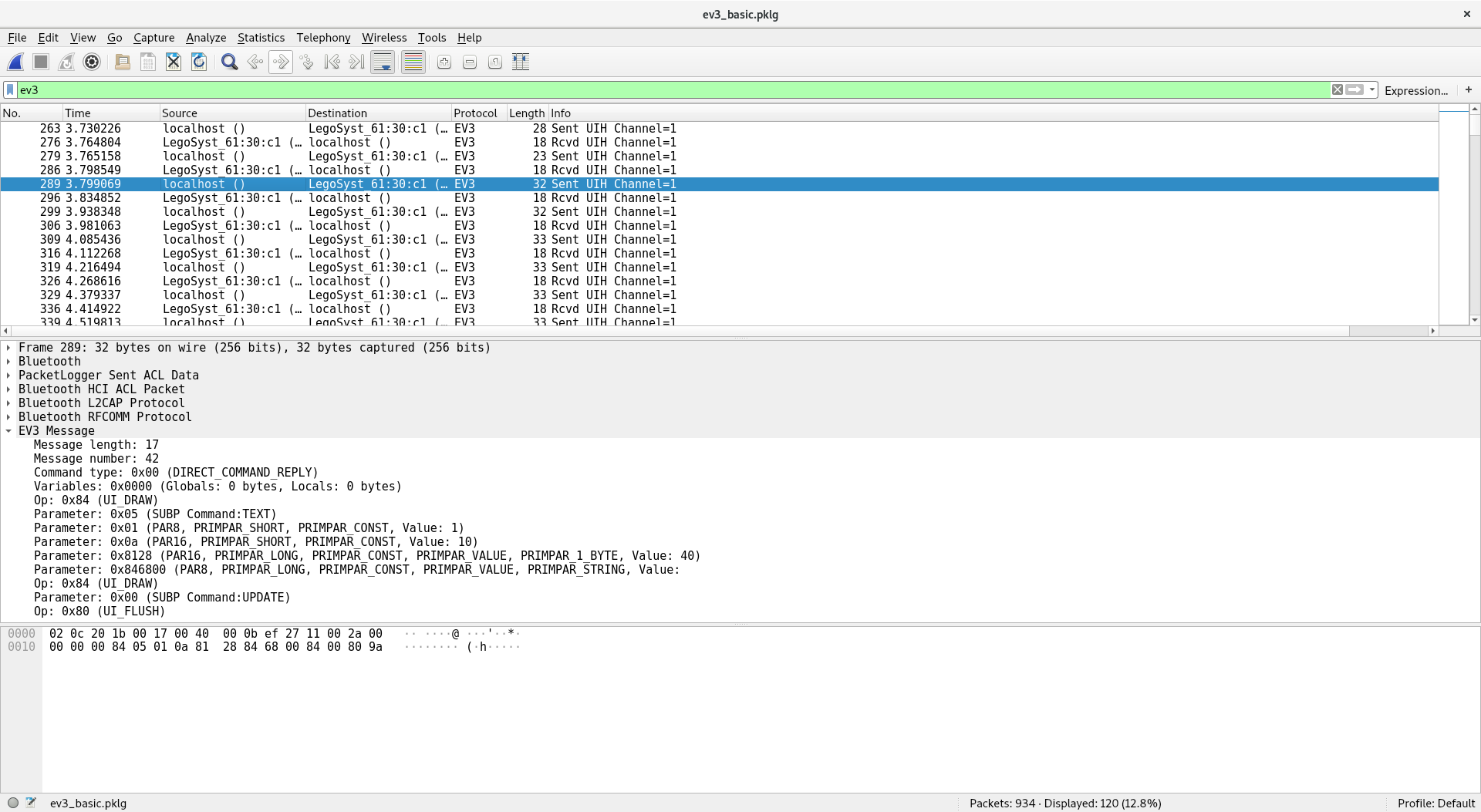
In the official Mindstorm source repository we can find what those parameters mean:
- CMD = TEXT
- \param (DATA8) COLOR - Color [BG_COLOR..FG_COLOR]\n
- \param (DATA16) X - X start cord [0..LCD_WIDTH]\n
- \param (DATA16) Y - Y start cord [0..LCD_HEIGHT]\n
- \param (DATA8) STRING - First character in string to draw\n
So now we know, that the second parameter is the column, the third one is the row and last but not least the fourth one is our character. Now we thought, nice we just export the packages and we can parse out the flag... Yeah first if you check the packages, the characters were not drown in the correct order, so you really need to use the coordinates, and unfortunately the dissector has some issues, and at least on my computer the parameters got not exported, so I just went through the packages noted the coordinates and the char in an Excel sheet and sorted them first after the rows and second after columns.
The flag was: hitcon{m1nd5t0rm_communication_and_firmware_developer_kit}